We protect your bottom line.
Cyber threats to your data and your business are getting more frequent and more efficient. A simple virus can cause employee downtime, but a complex, sophisticated ransomware can expose critical business information, and put a company at risk both legally and financially. A successful cyber attack can bring a successful business down. As a business owner, a CEO, or IT manager, it is important to take active measures to protect your valuable business information. Our CyberOne suite of attended services, software and appliances, is custom tailored to your business needs, providing adequate security at a reasonable cost. All services offered through CyberOne are fully attended, this means that we actively monitor your devices and take the necessary actions to ensure your network is safe. Looking for an always on, cyber security first co-managed solution to supplament your IT infrastructure? TechOne co-manages networks nation wide, with solutions such as: - Unified Threat Protection - Secured RMM. - Office 365 management and Azure AD. - Email and content filtering. - Advanced backup, both on and off site, VM, and immutable backup.
Benefits at a glance:
Partnering with TechOne provides your company with:
- 24/7 Managed Cyber Security.
- Managing and mitigating security incidents, including breaches.
- A dedicated team that understand your risk.
- Proactive, knowledgeable periodic network evaluation.
- Educating employees about cybersecurity best practices to reduce human errors.
CyberOne Managed Cyber Security

Cyber Attack Prevention and Response
Conduct security assessments for organizations, and design security systems and processes. Specialize in areas such as physical security, personnel security, and information security. Engineer, install, maintain, or repair security systems, programmable logic controls, or other security-related electronic systems.
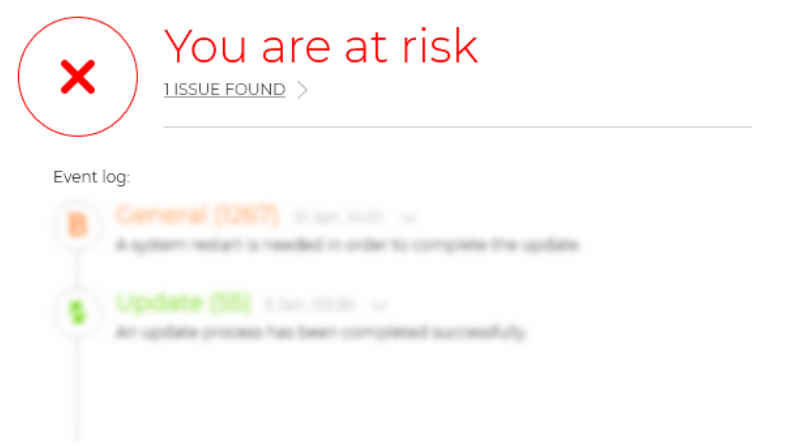
Anti-Everything Monitoring
Maintaining security not only for your organization, but also your employees, partners, and customers. By integrating ongoing cybersecurity monitoring into your business’ digital practices, you can monitor for cyber threats, data breaches, and security misconfigurations in real time.
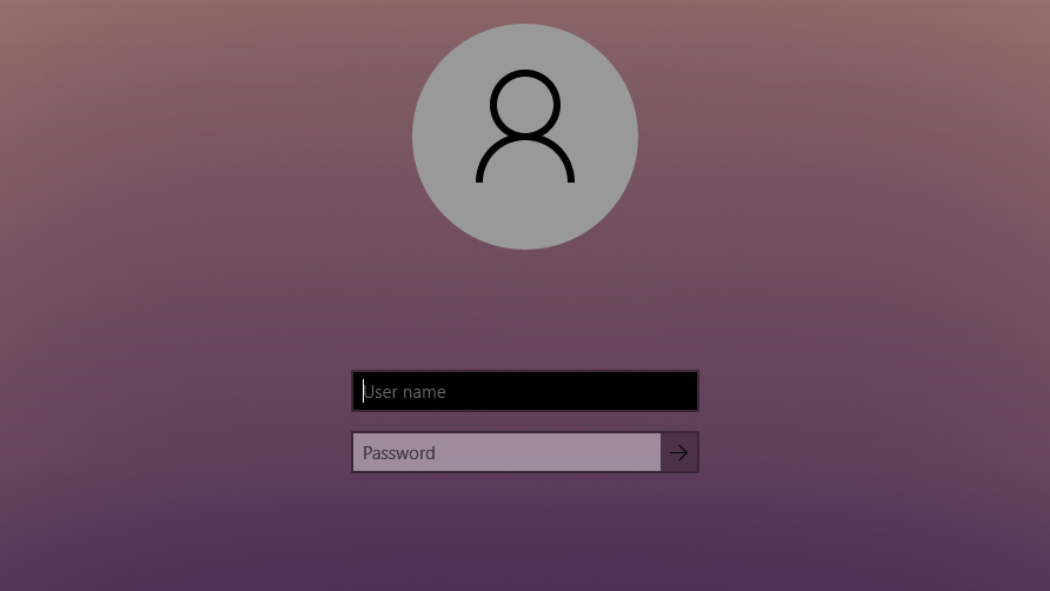
Data and Application Access Control
Access control minimizes the risk of authorized access to physical and computer systems, forming a foundational part of information security, data security and network security. Depending on your organization, access control may be a regulatory compliance requirement.

Cyber Perimiter Hardening
Cybersecurity involves preventing, detecting and responding to cyberattacks that can have wide-ranging effects on individuals, organizations, the community and at the national level.











